This article, based on initial research conducted by recently graduated Georgia Tech Cybersecurity Policy track Masters student Erin Whittaker, looks more closely at indictments in absentia as a way of deterring future attacks and creating accountability in cyberspace.
Over the past half-decade the United States government has used indictments in absentia as a form of deterrent for malicious cyber acts perpetrated by foreign actors who are not subject to U.S. jurisdiction. Arguably, indictments in absentia are one of the best methods for authoritatively attributing a cyber-attack to an actor because of the associated due process involved in collecting evidence and burden of proof standard (i.e., probable cause). However, critics argue that indictments in absentia are not an effective deterrent since it is very rare that the defendants charged appear in U.S. court.
The analysis uses a dataset derived from the United States Department of Justice’s (DoJ) press releases and indictments. Whittaker initially identified 34 indictments in absentia pertaining to cyber hacking, attacks, and espionage. A similar dataset was developed by Garret Hinck of the Carnegie Foundation’s Cyber Policy Initiative and published in a Lawfare blog. The data presented here reconciles and summarizes the datasets.
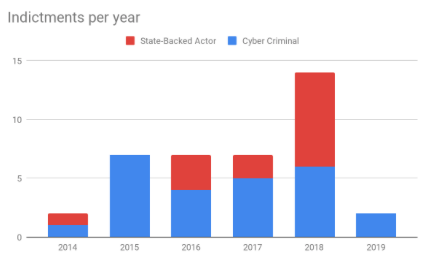
Figure 1
Figure 1 shows a total of 39 indictments since 2014. It differentiates between indictments, with defendants categorized as cyber criminals or state-backed actors. Twenty-five (64%) indictments accused the former, while fourteen (36%) involved the latter. It’s important to note that indictments do not always implicate a state. One example is the DoJ’s 2014 indictment against Su Bin, a Chinese national and businessman residing in Canada at the time. While his indictment included allegations of violations of the Computer Fraud and Abuse Act as well as export control regulations and linked him to unidentified co-conspirators, it never mentioned the Chinese government. However, it was widely reported that Bin was conducting espionage on behalf of the Chinese government. How should one categorize these indictments? In this analysis, Whittaker relied on the language in the indictments. Regardless, indictments of state-backed actors appear to be increasing while indictments of cyber criminals remains steady over the period studied.
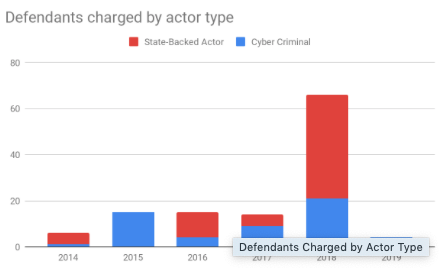
Figure 2 details the types and number of defendants accused. We see a total of 120 individuals accused, with a slight majority (66, 55%) being state-backed versus 54 (45%) being criminals. Indictments implicating a state average twice the number of defendants (4.71 versus 2.16) versus cyber crime indictments. Of note is the rapid growth in number of state-backed actors indicted, while the number of criminal actors has remained relatively smaller. This perhaps reflects the complexity of the underlying state-backed cyber-attacks (e.g., information operations) being investigated or the resources available to states.
Figure 2
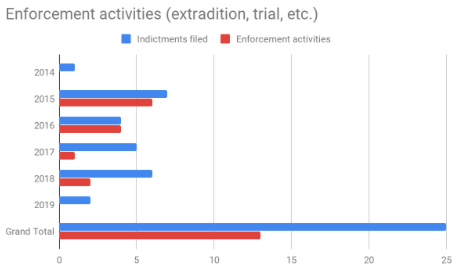
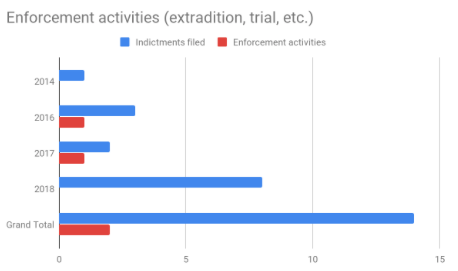
An indictment is a major, although only one, step in deterring future attacks. Arguably there is weaker deterrence if there are no consequences for the alleged perpetrators. Figure 3a and 3b compare indictments versus enforcement activities, including extraditions, arrests and convictions. As one would expect, indictments involving cyber criminals are more likely to result in enforcement activities. Far fewer enforcement activities occur (2) when states are implicated versus cyber criminals (13). This makes sense given the variety of bilateral and international mechanisms available to bring criminals to justice, while implicated states (and their agents) are far more likely to simply ignore allegations of illegal conduct. However, in both cases, the number of enforcement activities appears to be declining relative to indictments filed.
Figure 3a: Cyber criminal actor indictments
Figure 3b: State-backed actor indictments
What can we take away from the data? Based on this data, using indictments to identify individual perpetrator(s) and their state affiliations appears to growing. But it also appears that that alone is not capable of resulting in enforcement or accomplishing deterrence.